An Overview of Ukrainian Cybersecurity

Cybersecurity is important globally, but it will be even more so in Ukraine in 2025.
Lately, cyber-attacks are no longer just attacks of machines on machines; they are now intended for people and can impact them as well.
The use of the internet and other computer networks can be an additional weapon to disrupt the work of the state, sow mistrust, destroy infrastructure, and destabilize the country.
Therefore, cybersecurity involves diverse technologies that help secure various digital components, networks, data, and computer systems from unauthorized digital access.
In this article, we aim to review the Ukrainian path in the field of cybersecurity, its evolution, adaptability, how it faces challenges, and the impact of support provided by international partners.
The Evolution of Cybersecurity in Ukraine
Ukraine has been dealing with cyber threats for many years, but compared to today, resources dedicated to cyber security were more limited in the past.
We can define 3 phases of the evolution of Ukraine's cybersecurity strategies and capabilities, here they are:
Pre - 2010 Period
At this time, cybersecurity was still developing globally and Ukraine was no exception. Funding, expertise, and specialized institutions were just beginning to appear. However, the rapid evolution of the cyber threat and the growing geopolitical tensions in the region required a stronger, multilateral approach, which later took shape.
2014 - 2022
The annexation of Crimea and the conflict in Donbas marked a turning point in Ukrainian cybersecurity evolution. The country has faced an increase in cyberattacks, targeting the most important infrastructure and government systems.
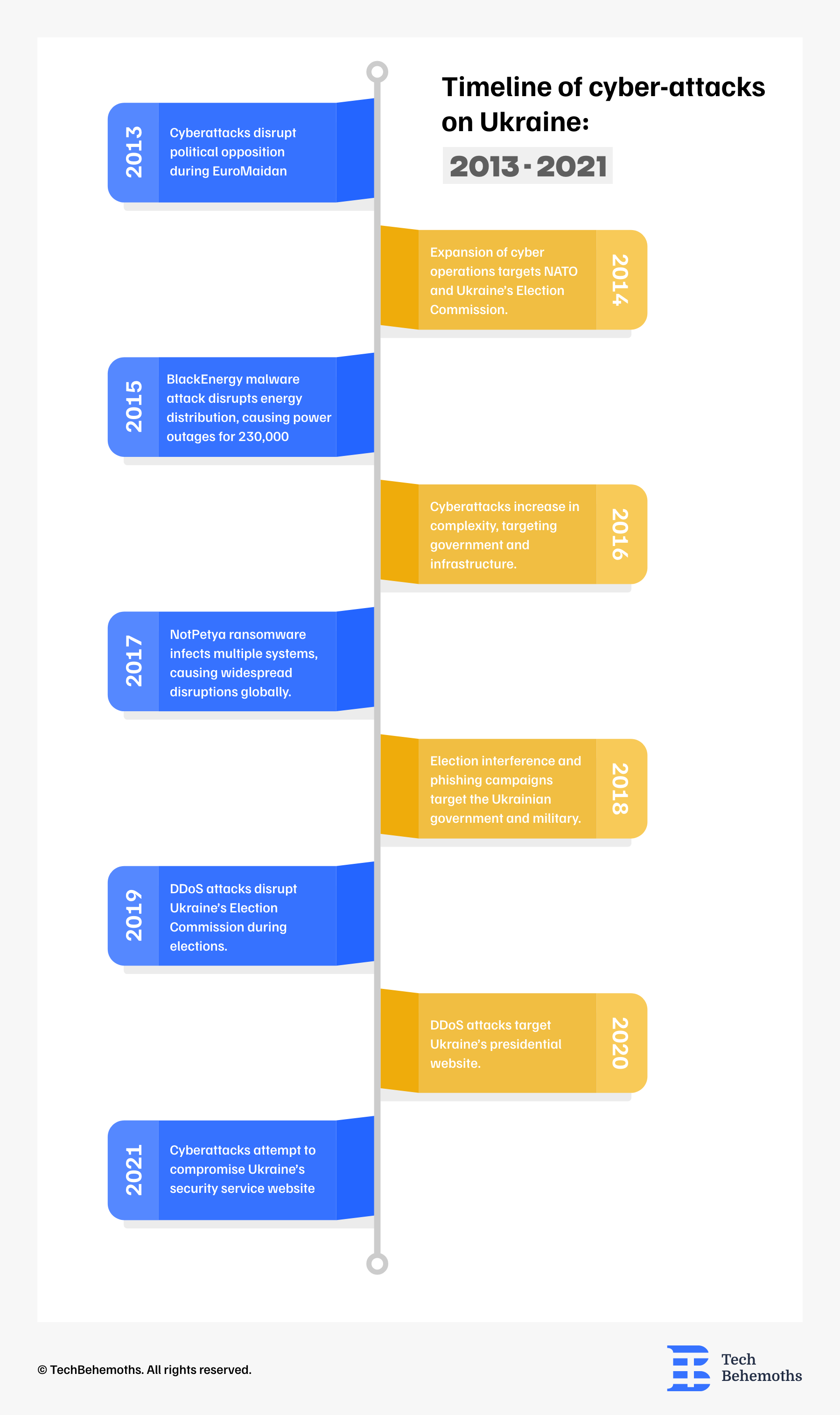
Key cyber incidents can be categorized in the following periods:
2013 - 2014 Cyberattacks were used to disrupt political opposition during Ukraine's EuroMaidan Revolution, hacking of Ukraine's election systems, and disinformation campaigns during Crimea's annexation.
2015 Russia carried out its first cyberattack on Ukraine's electricity grid with BlackEnergy malware, which affected over 230,000 residents.
2016 - 2017 Attacks became more advanced, with major ransomware attacks such as WannaCry and NotPetya causing global damage.
2018 - 2019 At the time, Ukraine was facing election-related cyberattacks and phishing campaigns targeting government and military data.
2020 - 2021 Ukraine's presidential website has been subjected to DDoS attacks and there have been attempts to compromise voter registries.
Source: https://cyberforumkyiv.org/A_Decade_in_the_Trenches_of_Cyberwarfare.pdf
2022 - Present
The 2022 Russian invasion dramatically escalated the cyberwar in Ukraine.
As the conflict is still ongoing, Ukraine continues to be the target of cyberattacks, mainly focused on government websites, energy and telecommunications providers, banks, media outlets, and more.
Here is a general overview of the most important cyber attacks in Ukraine from 2022 to 2025:
2022 Ukraine faced an increase in cyber attacks, including DDoS attacks against government websites and banks, and data-deleting malware designed to destroy data, just a month before Russia invaded the country. Also worth mentioning are the WhisperGate attack - intended to sow distrust among Ukrainians, and the Viasat Hack which disrupted satellite communications, impacting Ukrainian military capabilities.
2023 - 2025 (ongoing)
In the context of the conflict, four main types of cyberattacks are used against Ukraine:
- Destructive attacks - These aim to permanently destroy data or damage systems beyond repair.
- Disruptive attacks - These include methods like Denial of Service (DoS) to interrupt services and stop operations.
- Data weaponization -This involves stealing information for espionage or intelligence gathering.
- Disinformation campaigns - These spread Russian propaganda to mislead and influence people.
Case Study: Example of a Disinformation Campaign
Russia uses advanced tactics to spread false information and mislead both its citizens and people of other countries. These tactics seek to justify, for example, actions like the invasion of Ukraine.
This campaign of disinformation follows three clear steps:
1. The Preparation Part
Russia shares false stories in public discussions, similar to how Ukraine is a "failed state," controlled by "Nazis" or "radicals”.
2. Launch Part
The campaign starts at a strategic time. The goal is to spread these false stories through state media, social media, and other channels to reach as many people as possible.
3. Amplification Part
State-controlled media and related organizations push these messages further. They target specific groups to ensure that the disinformation spreads widely.
For example, Russian media may begin with official statements in press conferences, then use news outlets to publish stories that support the false narrative, and finally rely on foreign media to spread these misleading claims to global audiences.

Source: https://www.aljazeera.com/news/2022/2/24/putins-speech-declaring-war-on-ukraine-translated-excerpts
It is important to be informed about how a disinformation campaign works, to better discern the truth from the fake.
Ukrainian Cyber Defence
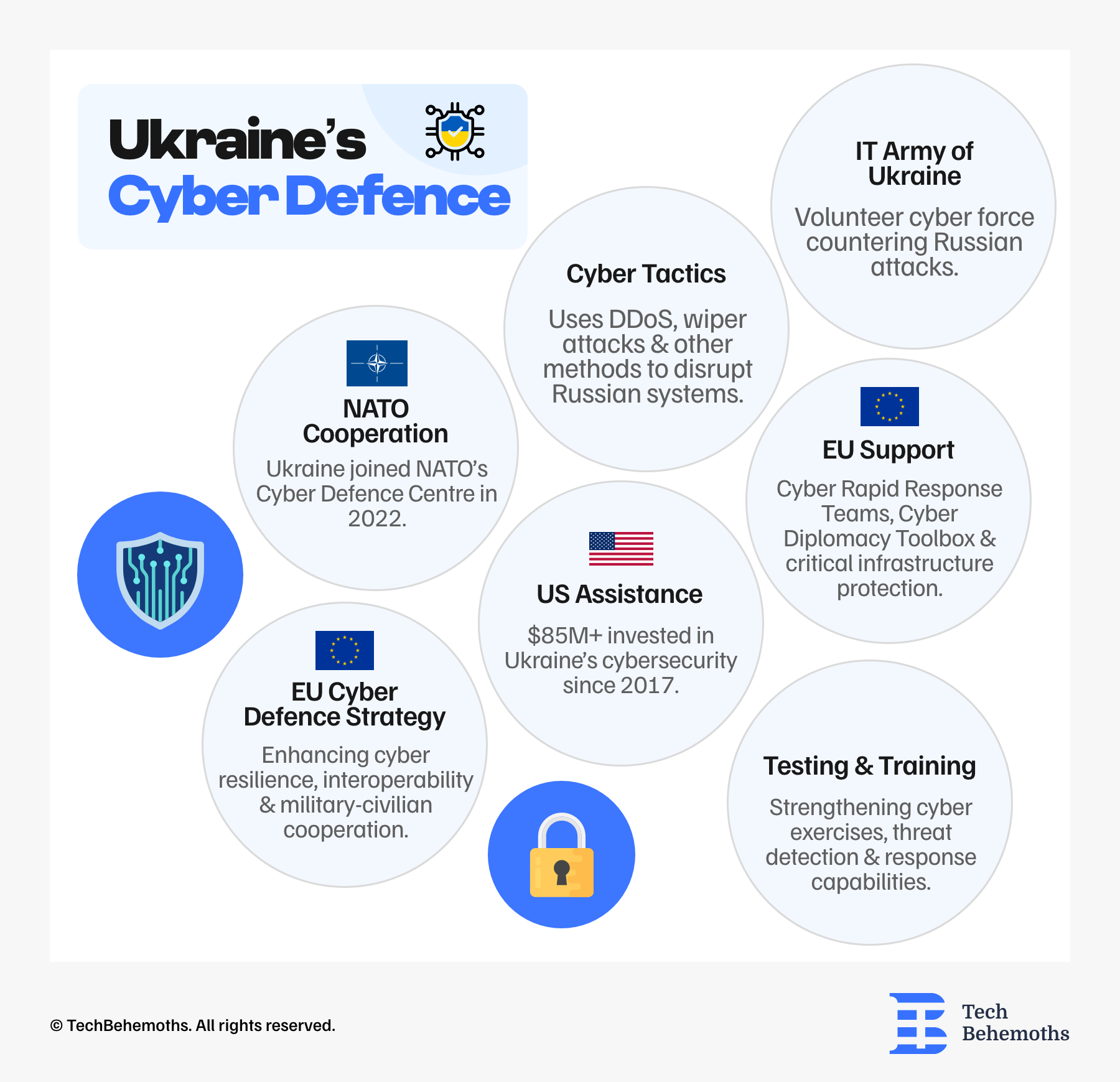
To defend against cyberattacks and strengthen national cybersecurity, Ukraine has received both international support and taken local measures.
Ukrainian IT Army
The Ukrainian government formed the IT Army of Ukraine at the end of February 2022 - composed of volunteers to respond to Russian cyberattacks, after the beginning of the Russian invasion of Ukraine on February 24, 2022.
The IT Army is led by the Ministry of Defence and includes volunteers from different areas of cyber security, economists, software developers, and moderators. They use methods such as DDoS attacks, which disrupt servers by overwhelming them with traffic, and wiper attacks that delete data. Their targets are Russia’s government, media, financial systems, power grids, and railways.
IT ARMY aims to help Ukraine win by crippling aggressor economies, blocking vital financial, infrastructural, and government services, and tiring major taxpayers. We also stop hostile media propaganda and spread the truth about the war.
IT Army - official website
International Support
The European Union (EU) fully supports Ukraine's resilience against cyberattacks and disruptions to critical infrastructure. In this sense, UE has initiated various measures, such as the EU-Ukraine Cyber Dialogue and Cyber Rapid Response Teams, to help Ukraine detect and mitigate threats.
The 3rd EU-Ukraine Cyber Dialogue took place in Brussels, Belgium, on 15 July 2024, where the EU and Ukraine agreed to collaborate more closely on cyber diplomacy, aiming to promote responsible behavior in cyberspace based on international law. The EU and Ukraine discussed strengthening cooperation to prevent and respond to cyber threats, focusing on protecting critical infrastructure, improving cyber risk awareness, and using the EU Cyber Diplomacy Toolbox.
The cyber rapid-response team (CRRT) is a team of cyber experts sent to help Ukraine defend itself against cyber attacks. This team includes eight to twelve specialists from Lithuania, Croatia, Poland, Estonia, Romania, and the Netherlands. They provide support both remotely and on-site in Ukraine.
In March 2022, Ukraine joined NATO's Cooperative Cyber Defence Centre of Excellence (NSDC). According to NSDC, this cooperation helps Ukraine and NATO better address shared cyber threats, including those from Russia.
Capability and knowledge come from experience, and Ukraine definitely has valuable experience from previous cyber-attacks to provide significant value to the NATO CCDCOE
Minister of Defence of Estonia Kalle Laanet
NATO together with the United States, contributed through funding, information sharing, and on-the-ground support. Since 2017, the US has invested $40 million in Ukraine's IT sector and with another $45 million in additional assistance in 2022 to strengthen Ukraine's cyber defensive capabilities.
The European Parliament encouraged the full implementation of EU cyber sanctions against entities responsible for attacks. The Parliament also recommended expanding the scope of EU missions to include combating hybrid threats, strengthening cybersecurity, and supporting Eastern Partnership countries such as Ukraine, Moldova, and Georgia.
Source: https://www.european-cyber-defence-policy.com/
Summing Up
What is clear is that cyberattacks are becoming more sophisticated every year, using advanced techniques and malware. However, the conflict in Ukraine is still ongoing, and cyber warfare is a dynamic and evolving aspect of it. New attacks are constantly occurring, and information is often not immediately released. Specific details about cyberattacks, their methods, targets, and attribution are often kept confidential for national security reasons and to avoid giving attackers an advantage.
However despite ongoing challenges, such as constantly evolving cyberattacks using advanced technologies, disinformation campaigns, a lack of qualified professionals, financial limitations, and infrastructure vulnerabilities, the Ukrainian cybersecurity defense sector has made notable progress through the years.
Of course, there are still areas for improvement, such as investing in advanced threat intelligence capabilities to anticipate and prevent attacks, strengthening cybersecurity education, and continuing collaboration with international partners to share best practices and resources.
What is certain is that Ukraine's lessons and strategies in this domain will undoubtedly be valuable for other nations facing similar cyber threats.